Kubernetes pipelines deal with an ever-escalating vary of threats that need extra integrated and automatic protection throughout the software lifecycle. Building items extra complex, crucial vulnerabilities can make their way into any phase of the pipeline: from develop to registry to check-and-staging to (in particular damaging) generation environments.
A single of the biggest roadblocks to successful Kubernetes pipeline protection has been investing the time to get it suitable. The intent of making use of containers is escalating the velocity of launch cycles, enabling extra up-to-date code and superior attributes with superior useful resource stabilization. Any handbook efforts to inject protection into this pipeline risk slowing that velocity and avoiding the advantages of a container method from staying completely understood.
DevOps teams just can’t find the money for to gradual down the pipeline. This is why automation is not just essential, but also the most sensible way to make sure container protection.
Kubernetes pipeline overview
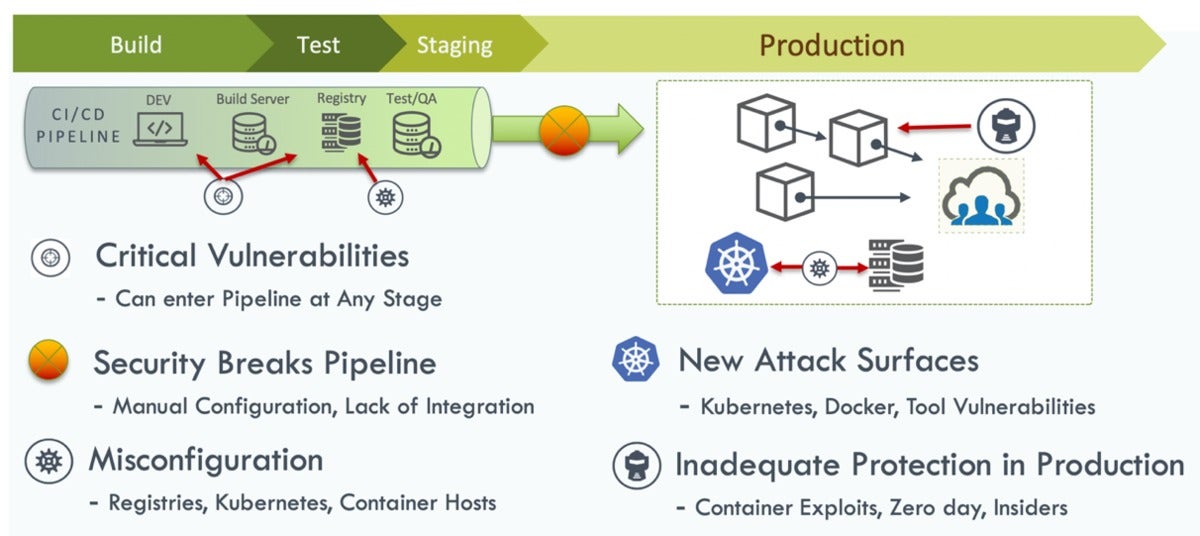
Having a action again, this is a simplified view of the Kubernetes pipeline, and some of the best threats at each and every phase:
 NeuVector
NeuVectorNew vulnerabilities can be introduced as early as the develop stage. (Open supply applications, in quite a few conditions, have been the culprit for including earlier-unidentified assault surfaces.) In a registry, even when you have productively removed vulnerabilities in the develop stage and stored a cleanse picture, a crucial vulnerability could possibly be uncovered afterwards that is influencing that picture. The same detail can (and consistently does) materialize with containers managing in generation.
In the generation natural environment, containers, crucial applications, or Kubernetes itself could be attacked, this kind of as we all noticed in very last year’s crucial API server vulnerability. All of this infrastructure presents an assault perimeter that demands to be monitored and safeguarded routinely. And, even when you do the finest possible position of eradicating vulnerabilities, there is continue to the hazard of zero-day attacks, unidentified vulnerabilities, or even insider attacks.
On the beneficial aspect, protection method can be integrated and automatic in the course of the Kubernetes pipeline.
10 actions to securing the container lifecycle
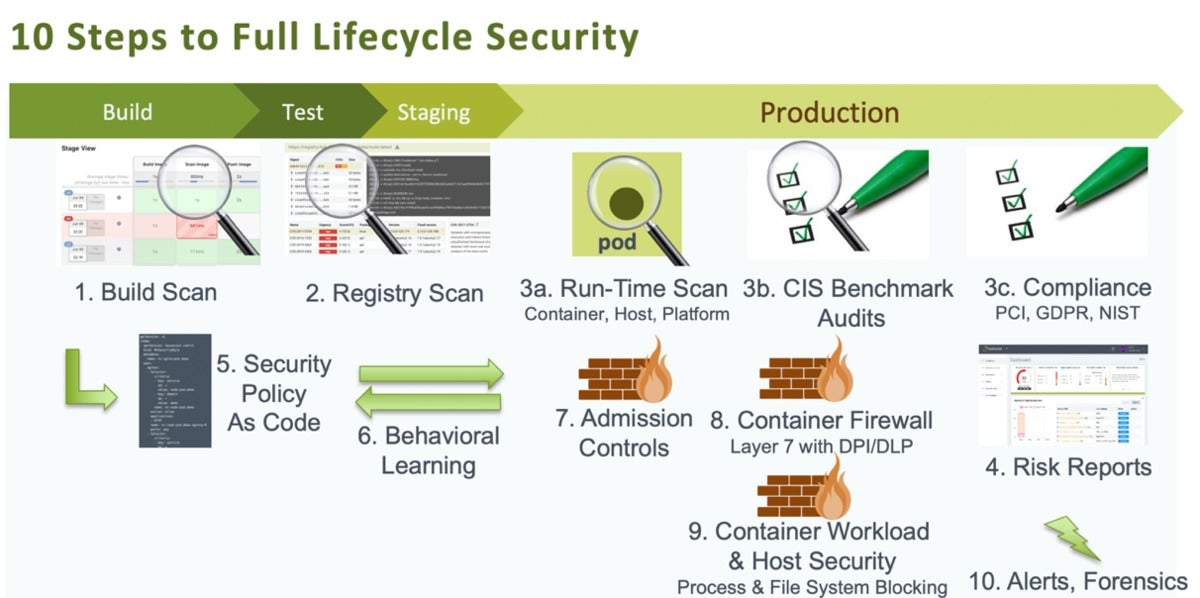
Right here are 10 particular strategies DevOps teams can integrate and automate protection throughout the entire lifecycle of their Kubernetes pipeline:
 NeuVector
NeuVectorAction one. Scan throughout the develop stage
This action is rather simple to automate, sending builds again to builders if there are any vulnerabilities or concerns.
Action two. Scan the registry
If new vulnerabilities are uncovered in the registry, that also can be alerted and despatched again to the dev crew for remediation. A single detail to recognize is that there is not generally a correct for a vulnerability, so you could have to allow it to be deployed into generation. Which is why generation vulnerability scanning and compliance evaluation are crucial as very well.
Action 3. Scan throughout runtime and run compliance checks
Vulnerability scanning in generation doesn’t just encompass containers. You generally want to be scanning the host and the orchestrator system (Kubernetes, OpenShift, and so on.) for vulnerabilities. The Docker Bench and Kubernetes CIS benchmarks are simple to run routinely and continuously. They’ll offer you with alerts any time a new container is deployed or a new host is added or patched.
For quite a few enterprises it’s also essential to be ready to do compliance reporting and management — which includes automatic segmentation that some field compliance prerequisites mandate. This is not something you’d want to do manually in any case, as quite a few runtime scanning and compliance checks frequently want to be automatic for compliance needs.
For case in point, the payment card industry’s PCI protection requirements demand segmentation and firewalling of in-scope and non-in-scope CDE website traffic. As you deploy pods managing on a host and in-scope, you can’t be shifting firewall procedures manually. Thus, PCI compliance (among the some others) necessitates automatic network segmentation.
Action 4. Run risk reviews
As any DevOps crew is aware of, risk reviews are crucial to managing the entire close-to-close vulnerability defense approach. Automating them only can make the approach that significantly more rapidly, dashing remediation anytime vital.
Action 5. Set protection plan as code, and
Action 6. Put into action behavioral studying
Stability plan as code and behavioral studying should really be utilised in tandem. Accomplishing so permits DevOps teams to build and deploy workload protection guidelines quite early in the progress approach and see them as a result of to generation environments. This important piece of automation nullifies the want to manually build procedures for shielding new apps (and nixes the affiliated slowdowns that results in).
Here’s a possible workflow. The DevOps and QA crew deploy an software into a testing/QA natural environment, wherever there is a container firewall able of behavioral studying. The container firewall learns all of that application’s container processes and typical file exercise, and produces plan procedures that can be exported to the dev crew to review and edit as necessary.
For case in point, there could want to be edits to the protocols the application makes use of, to the connections necessary, or to the processes that are likely to run in the application. People can now be developed as a protection manifest, which can be retested before generation deployment. In this way you can define not just workload particular guidelines but also world protection guidelines, like “No SSH is allowed in a container” or other this kind of procedures.
Action seven. Set admission controls
Integrating admission controls into your pipeline is a key action for ensuring automatic protection. Be guaranteed to apply the means to build admission command procedures that block any unauthorized deployments or vulnerable deployments into the generation natural environment.
Action eight. Put up a container firewall, and
Action 9. Automate container workload and host protection
As talked about higher than, applying a container firewall and implementing it to implement container workload and host protection offer important automatic protections for your pipeline.
This automation demands to consist of the means to implement protections at runtime — routinely blocking unauthorized network connections, processes, or file exercise, possibly in a container or on the host. These measures can also leverage network DLP to examine container website traffic for PII, credit score card information, account information, and extra delicate details, and to block any efforts to send out unencrypted information (avoiding it from staying stolen).
Action 10. Set alerts and forensics
At last, it’s precious to integrate and automate forensic abilities and warn responses. This could mean initiating an automatic packet seize on a suspicious pod that could have been hacked, or quarantining that container to block all network website traffic in or out of it. Accomplishing so can be achieved by environment plan procedures that specify the circumstances underneath which a packet seize or quarantine is initiated on a container.
Just about every phase of the Kubernetes pipeline is vulnerable without comprehensive safeguards. But DevOps teams really do not want to sacrifice the velocity of containerized progress if they know what can be automatic, why it’s crucial, and how to do it.
Gary Duan is co-founder and CTO of NeuVector. He has around fifteen several years of expertise in networking, protection, cloud, and information middle computer software. He was the architect of Fortinet’s award winning DPI item and has managed progress teams at vArmour, Fortinet, Cisco, and Altigen. His technological innovation knowledge contains IDS/IPS, OpenStack, NSX, and orchestration methods. He retains many patents in protection and information middle technological innovation.
—
New Tech Discussion board delivers a location to discover and focus on emerging organization technological innovation in unparalleled depth and breadth. The collection is subjective, based on our decide of the systems we think to be crucial and of greatest fascination to InfoWorld audience. InfoWorld does not settle for advertising collateral for publication and reserves the suitable to edit all contributed content material. Ship all inquiries to [email protected].
Copyright © 2020 IDG Communications, Inc.
