Firewall as a services (FWaaS), also recognised as a cloud firewall, is a services that supplies cloud-based community targeted traffic inspection abilities to prospects looking for to decommission or augment their existing community firewall appliances. This method lowers the stress on on-premises details middle gear and lowers the administration stress for internal cybersecurity teams.
FWaaS distributors differentiate their services choices by furnishing innovative community protection capabilities. These consist of likely past regular community targeted traffic inspection to consist of upcoming-technology firewall (NGFW) abilities. FWaaS distributors usually give intrusion avoidance and detection, software-informed protection plan enforcement, URL filtering, danger intelligence and innovative malware avoidance abilities.
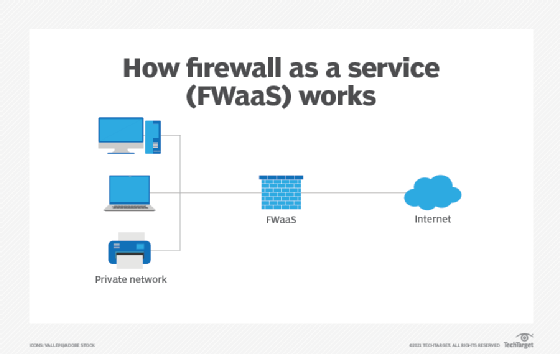
How does FWaaS perform?
FWaaS providers function in a manner identical to any other cloud infrastructure services. FWaaS distributors stand up details facilities with huge firewall implementations, acquiring major economies of scale. They then build virtual isolation among the providers provided to different prospects, avoiding protection troubles that may possibly occur if one particular shopper have been ready to modify a further customer’s configuration or examine their community targeted traffic.
Each shopper is then assigned a virtual occasion of the FWaaS services that they could modify as a result of a centralized console. Sellers ordinarily use the firewall configuration interfaces previously common to cybersecurity teams. In truth, prospects going from an on-premises appliance to an FWaaS services provided by the exact same vendor could be ready to use the exact same administration interface they use for their on-premises products.
Following configuring firewall principles that employ the organization’s protection plan, cybersecurity teams then modify community and DNS settings to flip the virtual change, routing targeted traffic as a result of the FWaaS vendor’s infrastructure for protection plan enforcement. At this stage, the FWaaS services replaces existing community perimeters as the first line of defense.
Why is FWaaS vital?
FWaaS platforms are actively playing an progressively vital function in cybersecurity programs because of to a few major things:
- Organizations are adopting cloud-first procedures wherever they search for to outsource infrastructure, program and other providers to cloud providers as significantly as attainable.
- Site visitors originating outside the house the corporation could continue to be in the cloud, bypassing on-premises details facilities and communications hyperlinks for remote and mobile people and cutting down the stress on neighborhood gear.
- Offloading a key protection services to a cloud company permits confined internal sources to concentration on other functions.
Rewards and disadvantages of FWaaS
Organizations weighing a likely move to a FWaaS presenting could be wanting to know irrespective of whether the timing is suitable for this type of move. Consider several vital rewards and disadvantages of these solutions:
- FWaaS choices give economies of scale, allowing for distributors to distribute the value of enhanced services choices across a lot of clients. Having said that, they also have the capacity to crank out more income by expanding their fees. Dependent upon the details of any negotiation, the net fiscal effect of a move could be insignificant or even maximize direct expenses.
- Adopting a FWaaS product or service permits an corporation to obtain entry to point out-of-the-art protection filtering technological innovation. Updates should occur in a fairly seamless vogue and businesses attract upon the deep know-how of the vendor in working its personal product or service.
- FWaaS choices are even now new in the market place. When some distributors have a handful of a long time of presenting these providers less than their belts, perimeter protection is a business-critical services and cybersecurity pros considering a services presenting have to be self-assured that the services is rock solid and will not disrupt business operations.
- As businesses move major parts of their working natural environment to the cloud, FWaaS supplies the benefit of cloud-indigenous These choices incorporate cloud abilities as baseline capabilities, allowing for teams to promptly safe their cloud operations.
FWaaS and SD-WAN
FWaaS services choices combine properly with program-described vast place networking (SD-WAN) procedures that search for to decentralize community targeted traffic routing. SD-WAN’s dynamic route optimization abilities makes it challenging to use regular community firewalls, which promptly develop into a chokepoint. FWaaS permits the firewall to exist as a cloud-based services, cutting down the dependency on the organization community. Jointly, FWaaS and SD-WAN are two foundational elements of the emerging community protection approach recognised as safe entry services edge (SASE).
Firewall-as-a-services distributors
Sellers across the protection spectrum now present cloud-based FWaaS methods. As the key cloud infrastructure distributors, AWS, Microsoft and Google all give firewall abilities for their personal environments but do not nevertheless present substantial-scale providers created to present NGFW functionality for on-premises targeted traffic. The key players in this market place are regular firewall distributors, together with:
- Palo Alto Networks
- Zscaler
- CheckPoint
- Cisco
- Barracuda Networks
- Cato
- Fortinet
